Page 160 - Computer_Science_F5
P. 160
router discards the packet and sends an congestion control algorithms namely;
ICMP Time Exceeded message to the Leaky Bucket Algorithms (LAB) and
source device. Token Bucket Algorithms (TBA). Chapter Three: Advanced Computer Networks
(e) Redirect (i) Leaky Bucket Algorithm (LAB):
FOR ONLINE READING ONLY
Purpose: To inform the source device of The LAB controls the rate at which data
a better route for sending packets. packets enter the network, smoothing
Process: If a router receives a packet out burst traffic and preventing network
and determines there is a more efficient overload. If data arrives faster than
route for future packets, it sends an ICMP the network can handle, the excess is
Redirect message to the source device. discarded to ensure efficient resource
utilisation. Data packets entering the
Congestion control network are like water flowing into the
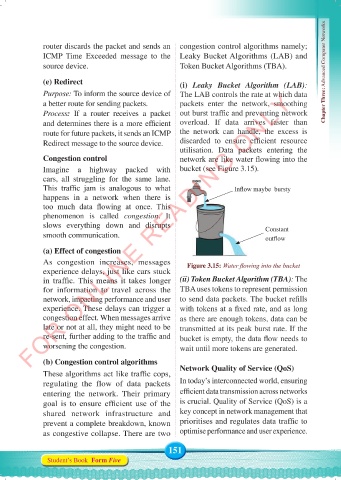
Imagine a highway packed with bucket (see Figure 3.15).
cars, all struggling for the same lane.
This traffic jam is analogous to what Inflow maybe bursty
happens in a network when there is
too much data flowing at once. This
phenomenon is called congestion. It
slows everything down and disrupts Constant
smooth communication. outflow
(a) Effect of congestion
As congestion increases, messages Figure 3.15: Water flowing into the bucket
experience delays, just like cars stuck
in traffic. This means it takes longer (ii) Token Bucket Algorithm (TBA): The
for information to travel across the TBA uses tokens to represent permission
network, impacting performance and user to send data packets. The bucket refills
experience. These delays can trigger a with tokens at a fixed rate, and as long
congestion effect. When messages arrive as there are enough tokens, data can be
late or not at all, they might need to be transmitted at its peak burst rate. If the
re-sent, further adding to the traffic and bucket is empty, the data flow needs to
worsening the congestion. wait until more tokens are generated.
(b) Congestion control algorithms Network Quality of Service (QoS)
These algorithms act like traffic cops,
regulating the flow of data packets In today’s interconnected world, ensuring
entering the network. Their primary efficient data transmission across networks
goal is to ensure efficient use of the is crucial. Quality of Service (QoS) is a
shared network infrastructure and key concept in network management that
prevent a complete breakdown, known prioritises and regulates data traffic to
as congestive collapse. There are two optimise performance and user experience.
151
Student’s Book Form Five
Computer Science Form 5.indd 151 23/07/2024 12:33