Page 210 - Computer_Science_F5
P. 210
it to pass through to your computer, to re-number when an organisation
depending on your firewall settings, changes its ISPs.
(d) It provides the ability to control (d) It is the perfect point to audit or log
access to the site system. It can Internet usage. Chapter Three: Advanced Computer Networks
significantly improve network (e) It can offer a central point of contact
FOR ONLINE READING ONLY
security and reduce risk to hosts for information delivery service to
on the subnet by filtering inherently customers.
insecure services.
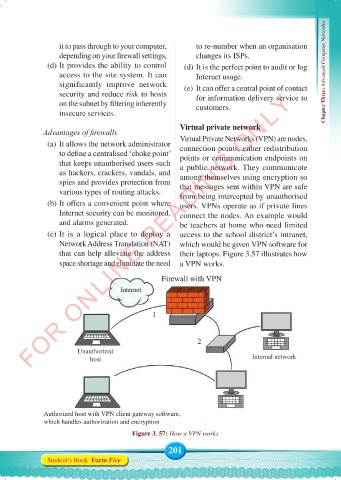
Virtual private network
Advantages of firewalls
(a) It allows the network administrator Virtual Private Networks (VPN) are nodes,
connection points, either redistribution
to define a centralised ‘choke point’ points or communication endpoints on
that keeps unauthorised users such a public network. They communicate
as hackers, crackers, vandals, and among themselves using encryption so
spies and provides protection from that messages sent within VPN are safe
various types of routing attacks. from being intercepted by unauthorised
(b) It offers a convenient point where users. VPNs operate as if private lines
Internet security can be monitored, connect the nodes. An example would
and alarms generated. be teachers at home who need limited
(c) It is a logical place to deploy a access to the school district’s intranet,
Network Address Translation (NAT) which would be given VPN software for
that can help alleviate the address their laptops. Figure 3.57 illustrates how
space shortage and eliminate the need a VPN works.
Firewall with VPN
Internet
1
2
Unauthorized
host Internal network
Authorized host with VPN client gateway software,
which handles authorization and encryption
Figure 3. 57: How a VPN works
201
Student’s Book Form Five
Computer Science Form 5.indd 201 23/07/2024 12:33