Page 154 - Computer_Science_F5
P. 154
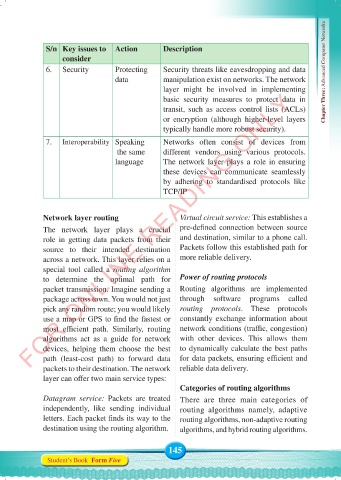
S/n Key issues to Action Description
consider
6. Security Protecting Security threats like eavesdropping and data Chapter Three: Advanced Computer Networks
data manipulation exist on networks. The network
layer might be involved in implementing
FOR ONLINE READING ONLY
basic security measures to protect data in
transit, such as access control lists (ACLs)
or encryption (although higher-level layers
typically handle more robust security).
7. Interoperability Speaking Networks often consist of devices from
the same different vendors using various protocols.
language The network layer plays a role in ensuring
these devices can communicate seamlessly
by adhering to standardised protocols like
TCP/IP
Network layer routing Virtual circuit service: This establishes a
The network layer plays a crucial pre-defined connection between source
role in getting data packets from their and destination, similar to a phone call.
source to their intended destination Packets follow this established path for
across a network. This layer relies on a more reliable delivery.
special tool called a routing algorithm
to determine the optimal path for Power of routing protocols
packet transmission. Imagine sending a Routing algorithms are implemented
package across town. You would not just through software programs called
pick any random route; you would likely routing protocols. These protocols
use a map or GPS to find the fastest or constantly exchange information about
most efficient path. Similarly, routing network conditions (traffic, congestion)
algorithms act as a guide for network with other devices. This allows them
devices, helping them choose the best to dynamically calculate the best paths
path (least-cost path) to forward data for data packets, ensuring efficient and
packets to their destination. The network reliable data delivery.
layer can offer two main service types:
Categories of routing algorithms
Datagram service: Packets are treated There are three main categories of
independently, like sending individual routing algorithms namely, adaptive
letters. Each packet finds its way to the routing algorithms, non-adaptive routing
destination using the routing algorithm. algorithms, and hybrid routing algorithms.
145
Student’s Book Form Five
Computer Science Form 5.indd 145 23/07/2024 12:33